By now, you probably heard about the cascade of data breaches that occurred ...
| Read
We all make choices about effort. There are only so many hours in a day, and ...
| Read
A discussion with Steve Bono, Founder and CEO of Independent Security ...
| Read
Clients frequently turn to us for advice on how to enhance the security of ...
| Read
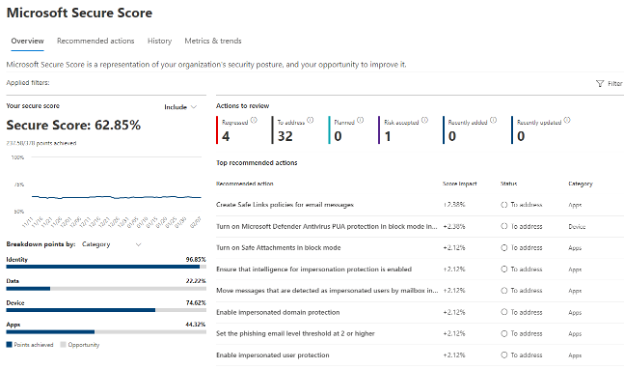
Effective security management relies on consistent disciplines like maintaining ...
| Read










.jpg)
