Social engineering is used by criminals to exploit the human elements of the security architecture of an organization. This happens by the attacker exploiting specific attributes and using psychology to bypass the technical security measures that are in place. These types of attacks can be difficult to combat because they don’t follow specific patterns or approaches. Because of this, social engineering is an extremely effective approach for compromising a business of any size. It’s effective because it takes advantage of the rights and privileges someone has. This blog will cover the different types of social engineering attacks, outline how social engineering works, and offers suggestions for how to combat social engineering attacks on your organization.
Types of social engineering attacks
Social engineering is a process used to exploit human psychology instead of advanced hacking methods. Social engineering has become an essential tool for cyberattacks in recent years, with companies such as Twitter, Shark Tank, and Toyota being breached by social engineering methods. There may have been more opportunities to perform social engineering as a result of the COVID-19 pandemic, with businesses being forced to have employees work from home where devices proved to lack the protection needed from malicious forces.
Social engineering helps attackers in a variety of ways. For example, human error can be used to initiate a cyber-attack. By using the victim’s legitimate access, attackers can infiltrate organizational networks, bypass their firewalls, infect systems with malware, and create back-doors into the network to maintain access.
There are a wide range of attacks. Some of the most popular include:
Phishing: typically starting as a scam email that lures the recipient into a trap. These emails often appear to come from an authentic source and ask the victim to click a link to claim a prize, approve a purchase, etc. This method relies on the idea that the recipient trusts the sender incorrectly.
Dumpster diving: this is exactly what it sounds like. This low-tech method to obtain information involves sourcing information on the potential victim by gathering thrown out documents such as bills, credit card information, or other types of confidential data. This is also the most common method for identity theft.
Scareware: in this type of attack, the attacker uses emotions to manipulate the user into installing malicious software by creating a pop-up that influences the recipient to perform an act out of fear or panic. In this scenario, the attacker only needs to convince the person to click on a link in the pop-up, which can be done through various techniques to influence the target.
Water hole: inspired by the hunting method users by predators in the wild, this attack method is a three-step process in which the attacker identifies the target organization and then observes the browsing habits of the company’s employees. Next, the attacker creates a website that looks like one often visited by the employees. Then, the attacker directs employees from the real site to the malicious site. The real goal is to get the victim to enter their credentials on an attacker-controlled page. Then the attacker uses those credentials to access the real system. Once the system is compromised, they can then infect other systems that are on the same network.
Reverse social engineering: these two step attacks are one of the simplest yet most effective at the organizational level. The attacker creates a problem for the intended victim, then they approach the target with the solution to their problem.
But how does social engineering work?
For social engineering to work, the attacker must form some type of influence on the targeted victim. The attacker initiates these attacks through behavioral aspects such as social influence, persuasion, trust, playing on emotions, behavior, decision making and reasoning, fraud, and language. The attacker is looking to exploit these attributes for their own benefit and can even use different vulnerabilities at various stages of the attack process.
First, the attacker is going to conduct research on their targeted organization. Then, they’re going to engage the potential victim in a variety of ways, including:
- Phishing
- Ransomware
- Trusted relationship
- Insider threat
- Deepfakes
One of the most common vulnerabilities is social influence. In these cases, the victim can be completely unaware that they are being influenced! This influence could be based on a reward being offered, or even someone pretending to be the victims’ boss or another person of authority, ordering them to take a specific action. Other examples include being influenced to buy something because it is perceived as being socially relevant or being influenced to join a group because it seems to be made up of likeminded people. All these types of influences can be dangerous because they require you to build social relationships, disclose personal information, and engage in a dialogue with the other person or party.
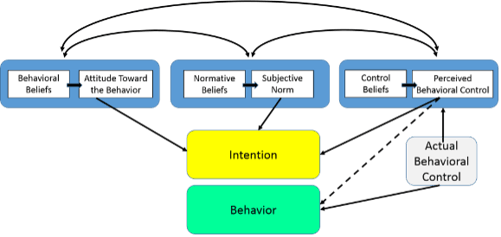
Social engineering relies heavily on methods of persuasion to manipulate the victims into revealing personal information or taking an action that results in them being hacked. Social engineering also relies on the theory of planned behavior. This theory states that the attitude toward the behavior defines the effort that an individual is willing to put into showing a certain behavior. The perceived behavior control indicates the level of control that a person has over a specific behavior. The makeup of this theory can be used to convince a victim to reveal personal information based on the behavioral stimulus (see graphic below). The methods used to influence the behaviors and attitudes of victims include the bystander effect, and cognitive dissonance theory, among others.
Bystander effect: when an individual is hesitant to help when bystanders are present. In the context of a social engineering attack, the target can be tempted to engage in a situation when in a group setting but is exploited later on once they’ve entered a private space and end up giving out private information.
Cognitive dissonance theory: the inner conflict when the behaviors and beliefs of an individual are not aligned. This conflict can influence one’s cognitive biases, such as decision making. In a social engineering attack, the attacker can exploit the cognitive biases to extract personal information about the victim.
Language is a key piece of an effective social engineering attack. Creating and elaborating information for these attacks relies heavily on the language the attacker is using when interacting with the target. We have established that effective cyberattacks on social engineering rely on human vulnerabilities and are exploited through human behavior, lack of knowledge, emotions, cognition, etc. All these methods also require trust. Building trust is one of the most crucial parts in a social engineering attack. A single social engineering attack can take place using multiple methods of influence, but a single influence method can exploit multiple human vulnerabilities. The multidimensional connections between the attacks, influence methods, and human vulnerabilities makes social engineering attacks extremely challenging for security professionals to protect against.
Responding to social engineering-based cyber attacks
Now that we have identified what social engineering is and how these types of attack happen, we must learn how to counter these cyberattacks. We’ve identified that the lack of human awareness is something that makes social engineering attacks successful. Social engineering methods focuses on hacking humans by targeting cognitive biases. Therefore, human awareness is a key factor in countering the social engineering attack. There are a few things your organization can do to protect against social engineering-based attacks:
- Have well-defined policies in place within your organization
- Communication Policies: Many social engineering attacks take place because the attacker exploited communication norms to conduct the attack. By having a communication policy for internal and external communication, a company greatly reduces the social engineering threat. These policies could include guidelines of what can and cannot be shared via electronic communication, approval processes for connecting personal devices to the company network, and work from home communications.
- Organizational Policies: These policies should cover having up to date and continuously monitored firewalls, spam filters, software updates, and making sure everything is installed properly on company provided devices, or personal devices if the device is used for work. It is recommended that a company provide devices as the company owned equipment can be managed by your IT department and easily monitored and updated when needed.
- Training new staff, and continuously training current staff
- Your team should be continuously learning about the threats that they face day to day, many of which they may not even be aware of.
- Having an in-house training or hiring a third-party organization to host a training for you can greatly increase your teams’ knowledge of social engineering threats, and greatly reduce the likelihood of your organization falling victim to a social engineering attack.
- Improve security awareness within your organization
- Have a systematic approach to identifying vulnerable employees and insider threats
- Analyze the security awareness of your workforce through testing
- Have routine system updates
- Evaluate your security infrastructure regularly
- Maintain consistent means for communication
The manipulation of human behavior, emotions, and psychology in cyberattacks presents an unknown and complex problem for security experts. Despite continuous advancements in security, humans will always be vulnerable. We must be able to effectively identify what a social engineering attack is before we can learn how to prevent one. Learning about social engineering and creating a cybersecurity approach within your organization that involves the human factors is a step towards having a strong and resilient cybersecurity framework.
Looking to learn about how resistant your organization is to social engineering? Reach out to contact@ise.io to chat to a member of the ISE security team about our wide range of security assessments and security consulting.


